What is OWASP ZAP?

OWASP ZAP (Zed Attack Proxy) is a widely used open-source security testing tool for finding vulnerabilities in web applications during development and testing phases. It is one of the many valuable resources provided by the Open Web Application Security Project (OWASP), a non-profit organization focused on improving the security of software.
Top 10 use cases of OWASP ZAP:
Here are the top 10 use cases for OWASP ZAP:
- Vulnerability Scanning: ZAP can scan web applications to identify common security vulnerabilities such as cross-site scripting (XSS), SQL injection, and cross-site request forgery (CSRF).
- Automated Testing: You can use ZAP to automate security testing by creating and running scripts to crawl a web application and detect vulnerabilities.
- Manual Testing: Security professionals and developers can use ZAP’s interactive tools to manually test web applications, providing more in-depth and customized security assessments.
- Spidering and Crawling: ZAP can automatically crawl a web application, discovering and mapping its structure and functionality for further testing.
- Fuzz Testing: ZAP supports fuzz testing, where it sends malformed or unexpected input to web forms and APIs to discover vulnerabilities related to input validation and handling.
- Session Management Testing: ZAP can help identify vulnerabilities related to how a web application manages user sessions, including session fixation and session hijacking issues.
- Authentication Testing: It can be used to test the security of authentication mechanisms, including brute force attacks, weak password policies, and insecure login mechanisms.
- API Security Testing: ZAP is capable of testing REST and SOAP APIs for security vulnerabilities, ensuring that API endpoints are secure from attacks.
- Web Services Testing: You can use ZAP to assess the security of web services and microservices, including XML and JSON-based communication.
- Reporting and Integration: ZAP provides detailed reports and can integrate with other tools and services, making it a valuable component of a comprehensive security testing and development pipeline.
OWASP ZAP is a versatile tool that can be employed in various stages of the software development lifecycle to help identify and address security vulnerabilities early, reducing the risk of security breaches and data leaks. It is a popular choice for both security professionals and developers striving to create more secure web applications.
What are the feature of OWASP ZAP?
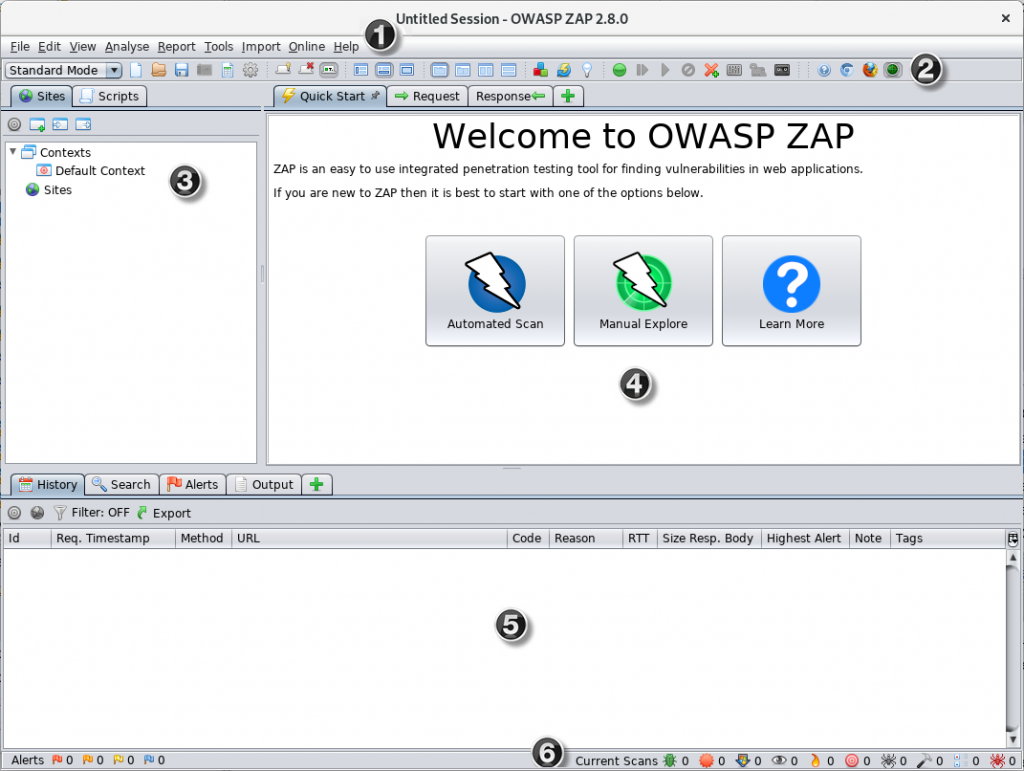
OWASP ZAP (Zed Attack Proxy) is a powerful tool for web application security testing. Its features and architecture are designed to help users identify and mitigate vulnerabilities in web applications. Here are some of the key features and an overview of how ZAP works:
Features of OWASP ZAP:
- Automated Scanning: ZAP can automatically scan web applications for common security vulnerabilities such as cross-site scripting (XSS), SQL injection, and more.
- Interactive Tools: It provides interactive tools for both manual and automated testing, allowing security professionals and developers to customize and extend their testing efforts.
- Proxy Mode: ZAP acts as an intercepting proxy, allowing users to inspect and modify web traffic between their browser and the target application. This is useful for identifying security issues in real-time.
- Spidering and Crawling: ZAP can crawl web applications to map their structure and discover new pages and functionality for testing.
- Fuzzing: The tool supports fuzz testing, sending malformed data to web forms and APIs to identify input validation and security issues.
- Scripting and Automation: Users can create and run scripts in various programming languages to automate repetitive testing tasks and customize ZAP’s behavior.
- Session Management Testing: ZAP helps identify vulnerabilities related to how web applications manage user sessions, including session fixation and hijacking.
- Authentication Testing: It can test authentication mechanisms, including brute force attacks, weak password policies, and authentication bypass vulnerabilities.
- API Testing: ZAP supports testing REST and SOAP APIs for security vulnerabilities, ensuring API endpoints are secure.
- Plug-in Support: ZAP’s extensible architecture allows users to develop and install custom plug-ins to enhance functionality and integrate with other tools and services.
How OWASP ZAP Works and Architecture?
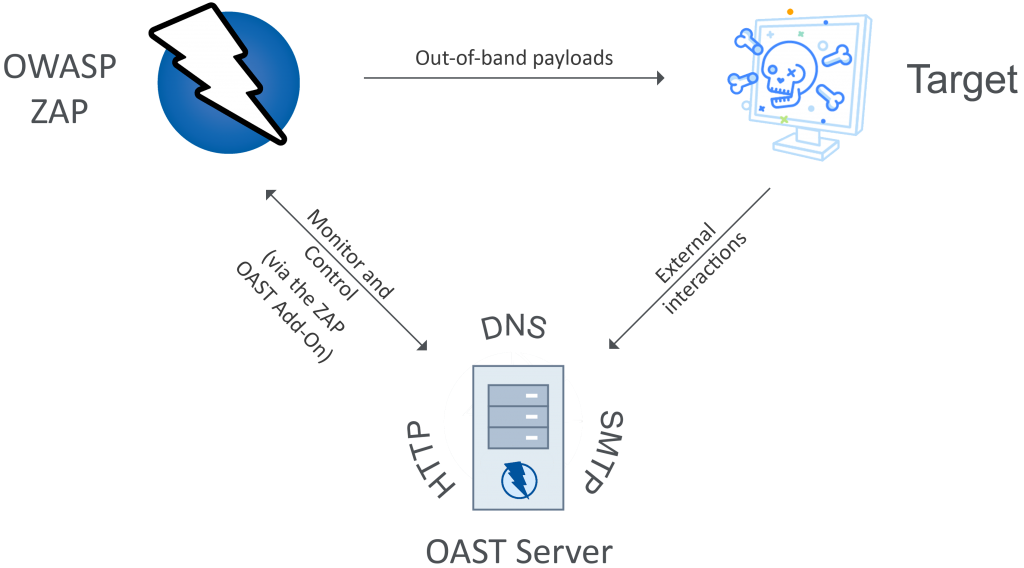
OWASP ZAP follows a proxy-based testing approach, which means it sits between the user’s browser and the target web application, intercepting and inspecting traffic. Here’s a simplified overview of its architecture and how it works:
- Proxy Mode: ZAP acts as an intercepting proxy, capturing HTTP and HTTPS traffic between the user’s browser and the target web application.
- Spidering and Crawling: ZAP can automatically crawl the target application by following links and identifying new pages and endpoints.
- Active Scanning: ZAP performs active scanning, where it sends various payloads and probes to the application to identify vulnerabilities. This includes SQL injection, XSS, and other attacks.
- Passive Scanning: ZAP also performs passive scanning by analyzing the captured traffic for potential vulnerabilities and security issues.
- Reporting: ZAP generates detailed reports highlighting vulnerabilities, their severity, and recommendations for remediation. These reports can be exported in various formats.
- Interactive Testing: Users can interact with the tool to manually test the application, using features like the “Break” mode to pause and modify requests and responses in real-time.
- Scripting and Automation: ZAP allows users to create scripts to automate testing scenarios, extending its capabilities beyond the built-in features.
- Plug-ins: Users can install and develop custom plug-ins to add new features, integrate with other tools, and enhance ZAP’s functionality.
OWASP ZAP is a flexible and extensible web application security testing tool that leverages proxy-based interception, automated scanning, and interactive testing to identify and address security vulnerabilities in web applications effectively. Its architecture allows for customization and integration with other security tools and services.
How to Install OWASP ZAP?
To install OWASP ZAP, you can download the installer from the OWASP ZAP website. The installer is available for Windows, macOS, Linux, and Docker.
Once you have downloaded the installer, follow the steps below to install OWASP ZAP:
On Windows:
- Double-click on the OWASP ZAP installer to open the InstallShield Wizard.
- Implement the on-screen instructions to complete the installation.
On macOS:
- Open a Finder window.
- Navigate to the directory where you downloaded the OWASP ZAP installer.
- Double-click on the OWASP ZAP installer to open the installation wizard.
- Implement the on-screen instructions to complete the installation.
On Linux:
- Open a terminal window.
- Navigate to the directory where you downloaded the OWASP ZAP installer.
- Run the following command to install OWASP ZAP:
sudo sh zaproxy-<version>-<platform>.runCode language: HTML, XML (xml)Replace <version> with the version of OWASP ZAP you are installing, and replace <platform> with your operating system platform.
On Docker:
- Run the following command to start an OWASP ZAP Docker container:
docker run -it -p 8080:8080 owasp/zap2dThis will start an OWASP ZAP container on port 8080. You can then access the OWASP ZAP web interface at http://localhost:8080.
Once OWASP ZAP is installed, you can start scanning your web applications for vulnerabilities.
Basic Tutorials of OWASP ZAP: Getting Started
Let’s have a look at a stepwise basic tutorial of OWASP ZAP:
1. Start ZAP.
Once you have installed OWASP ZAP, you can start it by opening the ZAP desktop application or by running the ZAP command-line tool.
2. Create a new session.
When you start ZAP, you will be prompted to create a new session. A session is a collection of settings and data for a particular web application or group of web applications.
3. Import your web application.
Once you have created a new session, you can import your web application into ZAP. To do this, you will need to provide ZAP with the URL of your web application.
4. Start a scan.
Once you have imported your web application, you can start a scan to identify vulnerabilities. To do this, click on the Spider tab in the ZAP desktop application or run the zap-spider command-line tool.
5. Review the scan results.
Once the scan has completed, you can review the results in the ZAP desktop application or by viewing the ZAP report. The scan results will show you which vulnerabilities were found in your web application.
6. Remediate vulnerabilities.
Once you have identified vulnerabilities, you need to take steps to remediate them. This may involve patching software, updating firmware, or implementing security controls.
Here is a simple example of how to use OWASP ZAP to identify and remediate vulnerabilities:
- Create a new session for your web application.
- Import your web application into ZAP.
- Start a spider scan.
- Review the scan results.
- Identify any vulnerabilities that need to be remediated.
- Prioritize the remediation of vulnerabilities based on their severity and risk.
- Take steps to remediate the vulnerabilities.
- Run the spider scan again to verify that the vulnerabilities have been remediated.
You can repeat this process on a regular basis to ensure that your web applications are protected from known vulnerabilities.
Additional tips for using OWASP ZAP:
- Use ZAP to scan your web applications both before and after they are deployed to production.
- Use ZAP to scan your web applications on a regular basis to identify new vulnerabilities.
- Use ZAP’s reporting features to track your vulnerability management progress and identify trends.
- Use ZAP to integrate with other security tools, such as SIEM systems and ticketing systems.

👤 About the Author
Ashwani is passionate about DevOps, DevSecOps, SRE, MLOps, and AiOps, with a strong drive to simplify and scale modern IT operations. Through continuous learning and sharing, Ashwani helps organizations and engineers adopt best practices for automation, security, reliability, and AI-driven operations.
🌐 Connect & Follow:
- Website: WizBrand.com
- Facebook: facebook.com/DevOpsSchool
- X (Twitter): x.com/DevOpsSchools
- LinkedIn: linkedin.com/company/devopsschool
- YouTube: youtube.com/@TheDevOpsSchool
- Instagram: instagram.com/devopsschool
- Quora: devopsschool.quora.com
- Email– contact@devopsschool.com

